Defend Your Device: Safeguard Against Compromised Android Apps Today!
Android Apps Compromised: The Hidden Dangers of Mobile Security
A Glimpse into the World of Android Apps Compromised
Dear Readers,
3 Picture Gallery: Defend Your Device: Safeguard Against Compromised Android Apps Today!
Welcome to our in-depth exploration of the alarming issue of Android apps compromised. In this article, we will delve into the hidden dangers lurking within the world of mobile security, shedding light on the threats faced by millions of smartphone users worldwide. Brace yourself for a comprehensive analysis and gain valuable insights to protect yourself from falling victim to these malicious attacks.
Introduction: Understanding the Perils of Android Apps Compromised
Android apps compromised refer to the infiltration of malicious software into unsuspecting users’ smartphones or tablets. These compromised apps are often disguised as legitimate applications, enticing users with promises of enhanced functionality or entertaining features. However, beneath the surface, these apps harbor dangerous elements that can compromise the privacy, security, and overall functionality of users’ devices.
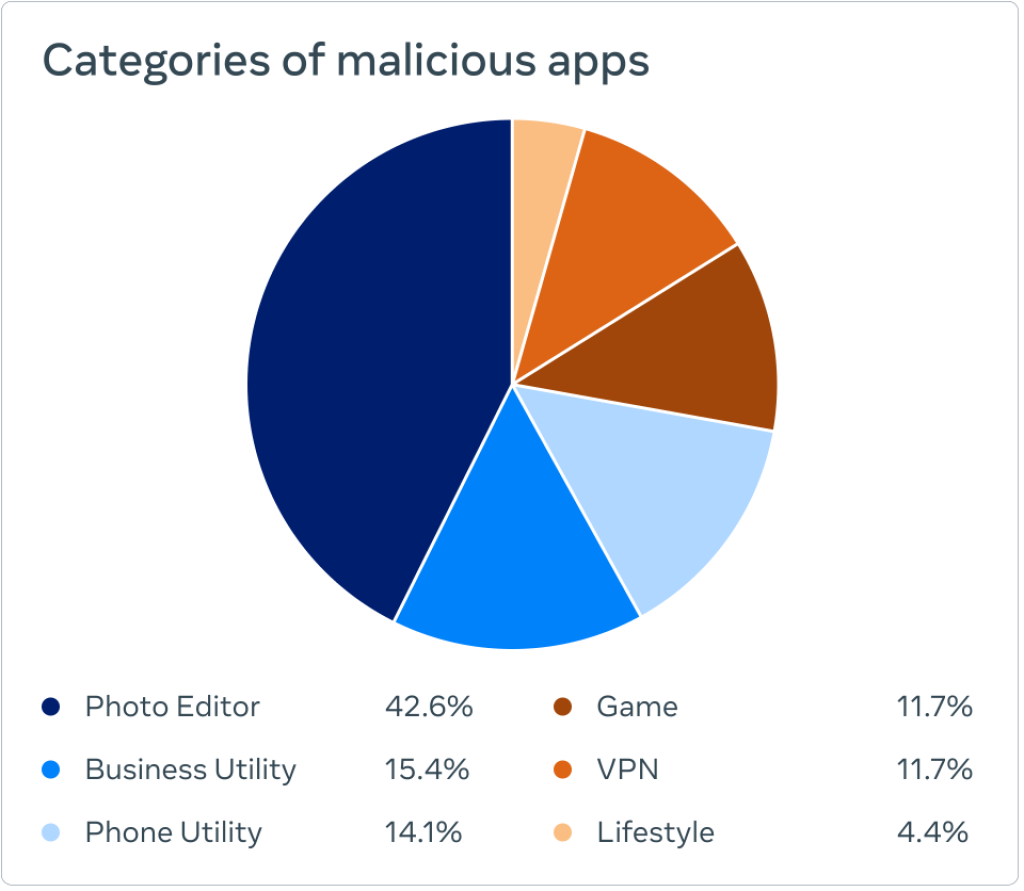
Image Source: about.fb.com
The Android operating system, known for its open-source nature, offers a vast array of applications available for download on the Google Play Store and third-party platforms. While this freedom of choice is undoubtedly advantageous, it also exposes users to potential risks, as developers can exploit vulnerabilities present in poorly regulated app stores.
Now, let’s delve deeper into the what, who, when, where, why, and how of Android apps compromised.
What are Android Apps Compromised?
🔍 Android apps compromised refer to applications that have been tampered with, allowing attackers to gain unauthorized access to users’ devices and personal information. These compromised apps can be downloaded from both official and unofficial sources, making it crucial to exercise caution when installing new applications.
Who is Behind Android Apps Compromised?

Image Source: futurecdn.net
👤 The perpetrators behind these malicious apps vary, ranging from individual hackers to organized cybercriminal groups. Their motivations may include financial gain, data theft, or even political espionage. These malicious actors exploit vulnerabilities in both the Android operating system itself and the apps available on the market.
When and Where Do Android Apps Compromised Occur?
📅 Android apps compromised can occur at any time and in any location where users download and install applications. While the Google Play Store has stringent security measures in place to detect and remove malicious apps, the risk remains due to the vast number of third-party app stores and websites that offer Android apps.
Why Are Android Apps Compromised a Growing Concern?
❓ The rise of Android apps compromised can be attributed to several factors, including the increasing popularity of Android devices, the lucrative nature of cybercrime, and the evolving sophistication of hackers. As a result, users must remain vigilant and adopt proactive security measures to safeguard their devices and data.
How Do Android Apps Compromised Operate?
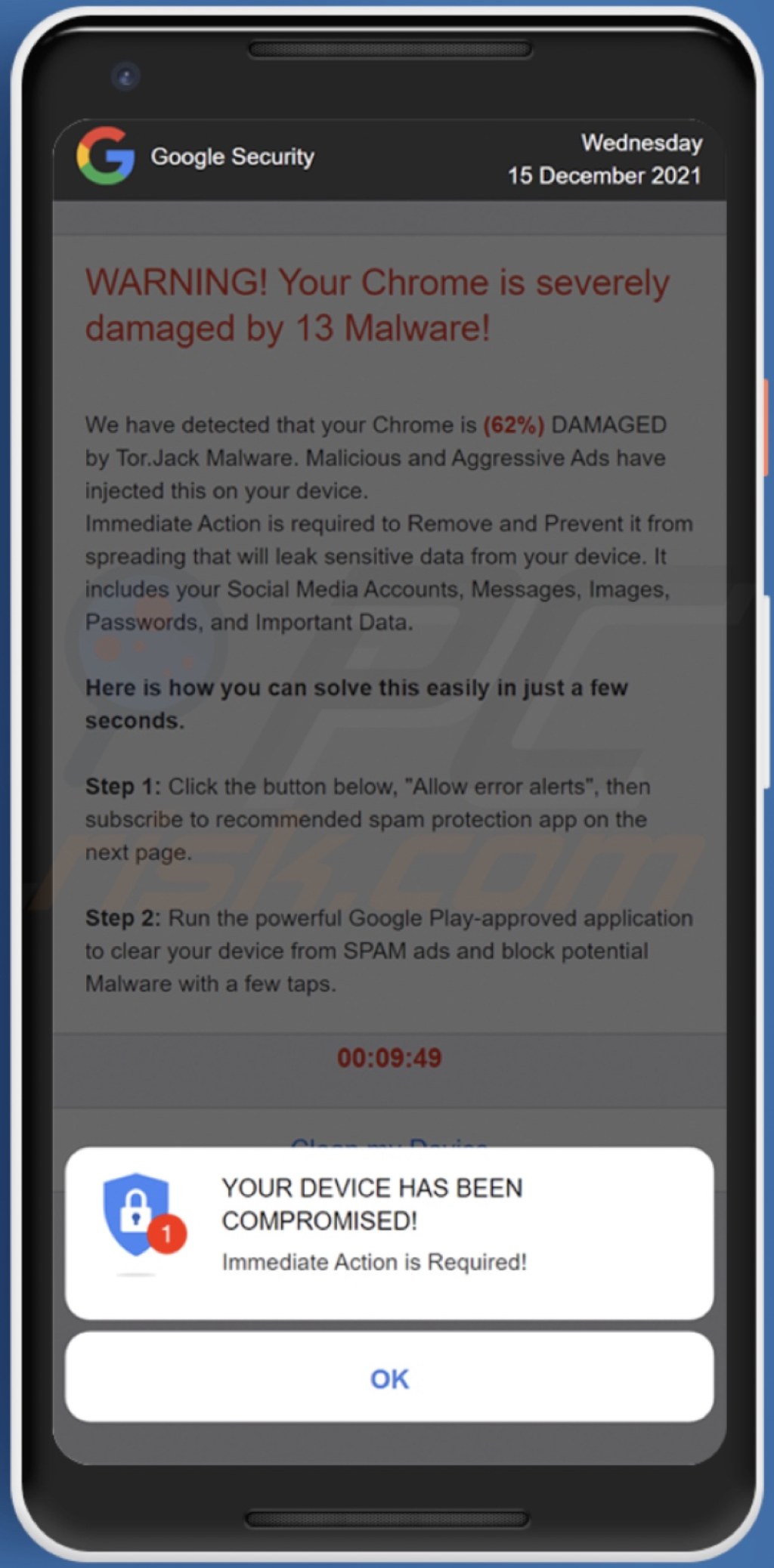
Image Source: pcrisk.de
🔐 Android apps compromised exploit various techniques to gain unauthorized access, such as the injection of malicious code, repackaging of legitimate apps with added malware, and even the exploitation of system vulnerabilities. Once installed on a user’s device, these compromised apps can collect sensitive information, track user activity, and even gain control over the device itself.
Advantages and Disadvantages of Android Apps Compromised
Advantages:
1. Enhanced functionality: Some compromised apps offer features not available in legitimate versions, enticing users to download them.
2. Access to premium content: Users may gain access to paid content for free, albeit at the risk of compromising their device’s security.
3. Customizability: Certain compromised apps allow users to personalize their devices to a greater extent than legitimate apps.
Disadvantages:
1. Privacy breaches: Compromised apps can access personal data, including contacts, messages, and browsing history, exposing users to identity theft and invasion of privacy.
2. Malware infections: Android apps compromised often contain malware, which can result in device slowdowns, unstable performance, and even complete device compromise.
3. Financial loss: Some compromised apps are designed to steal sensitive financial information, leading to unauthorized transactions and monetary losses.
Frequently Asked Questions about Android Apps Compromised
1. ❔ Can I trust apps downloaded from the Google Play Store?
✅ Yes, the Google Play Store has robust security measures in place to detect and remove malicious apps. However, it’s always important to read reviews and verify the app’s credibility before installation.
2. ❔ Is sideloading apps from third-party stores safe?
❌ Sideloading apps from unofficial sources increases the risk of downloading compromised apps. Stick to official stores whenever possible.
3. ❔ How can I detect if an app is compromised?
✉️ Look out for warning signs such as excessive permissions, poor reviews, or suspicious behavior. Install a reputable mobile security app for added protection.
4. ❔ Can compromised apps be removed?
🗑️ Yes, compromised apps can be uninstalled like any other app. However, it’s crucial to run a thorough device scan afterward to ensure complete removal of any associated malware.
5. ❔ How can I protect myself from Android apps compromised?
🛡️ Regularly update your device’s operating system and apps, install a reputable mobile security app, avoid sideloading apps from unofficial sources, and exercise caution when granting permissions to apps.
Conclusion: Safeguard Your Digital Life from Android Apps Compromised
Dear Friends,
Now that we’ve explored the perils of Android apps compromised, it’s crucial to take action to protect ourselves and our devices. By remaining vigilant, practicing safe app installation habits, and equipping ourselves with robust mobile security solutions, we can minimize the risk of falling victim to these malicious attacks. Prioritize your digital safety and enjoy a worry-free mobile experience.
Final Remarks: Your Security Matters
Throughout this article, we have highlighted the dangers of Android apps compromised and the steps you can take to mitigate these risks. However, it’s important to remember that no security measure is foolproof, and new threats are continually emerging.
Stay informed, stay proactive, and embrace a security-conscious mindset to safeguard your digital life. Together, we can navigate the complex landscape of mobile security and protect ourselves from the hidden dangers of Android apps compromised.
This post topic: Android Apps